Secure AI technology and self-defense AI cybersecurity
Graphen Alice Scurity provides a suites of next-gen AI powered solutions and products that protect an organization from inside and out.
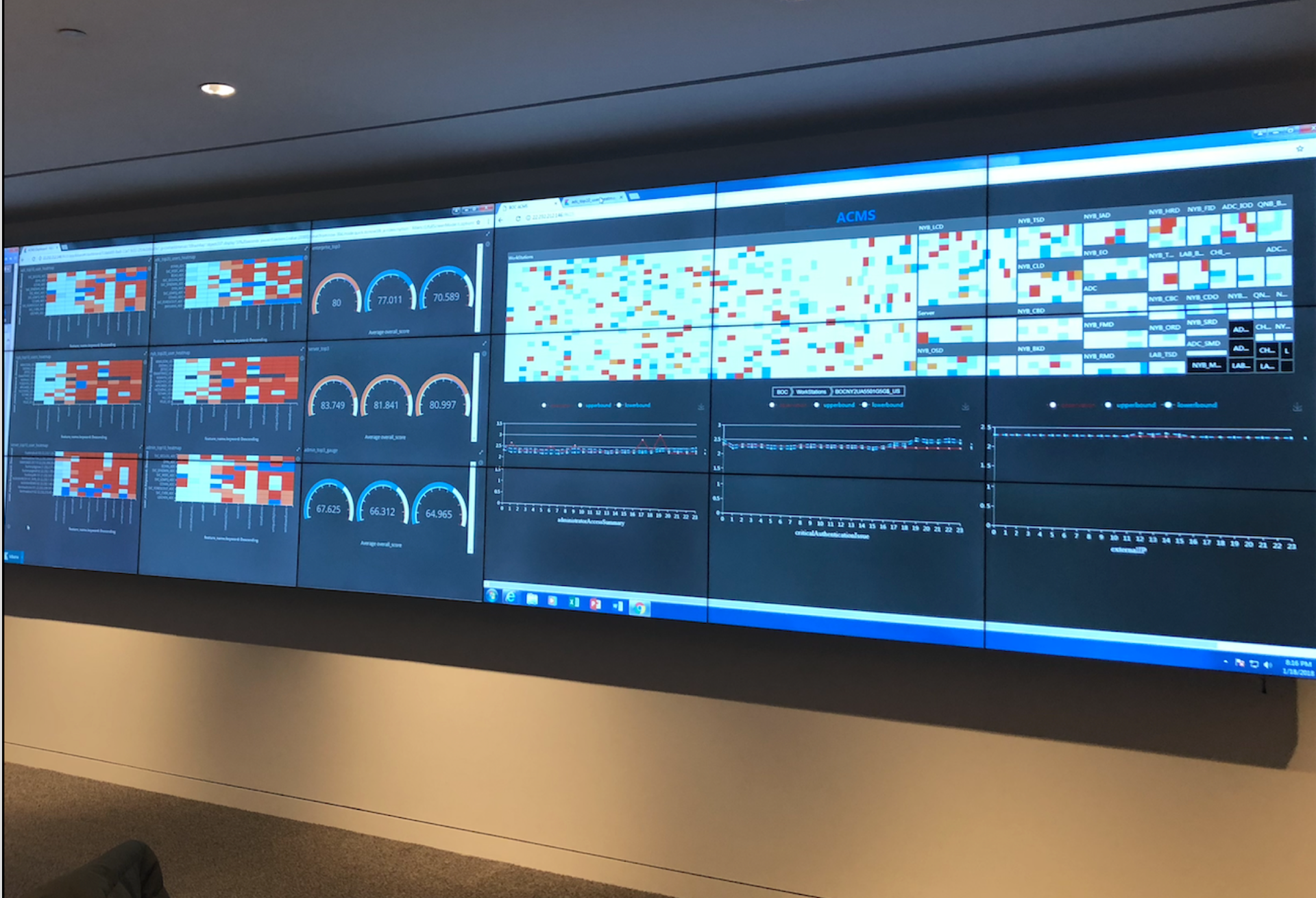
Alice Cyber Immune is a user behavior analytics-based cybersecurity monitoring system that detects insider threats and gathers all relevant and available information about users, devices, applications and network, detecting anomalies at various levels.
It provides an aggregate risk assessment to predict cybersecurity risks of all entities within the organization.
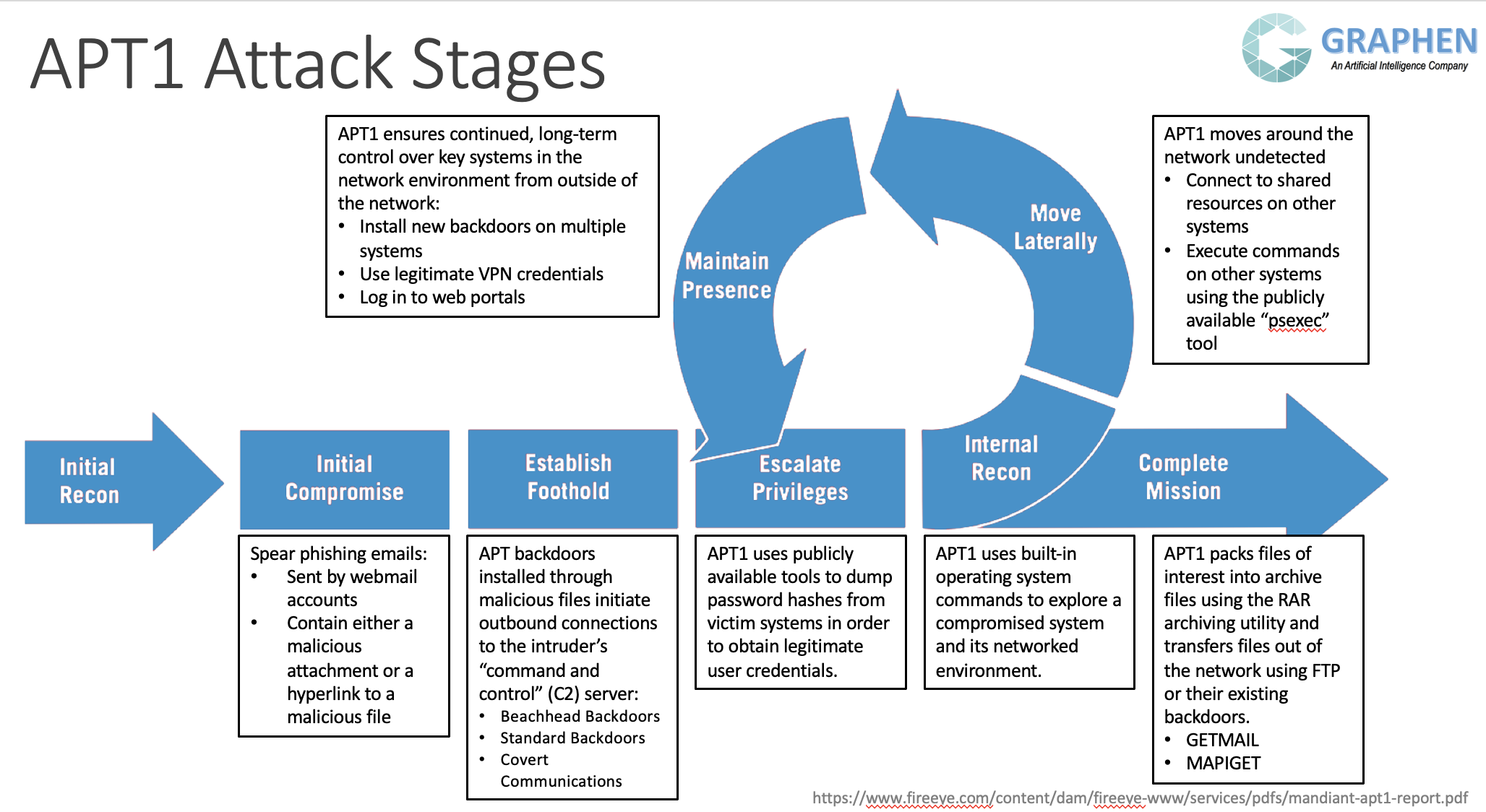
Advanced persistent threats (APTs) are attacks that gain an unauthorized foothold for the purpose of executing an extended, continuous attack over a long period of time. According to MITRE ATTACK®, a globally-accessible knowledge base of adversary tactics and techniques based on real-world observation, there are 110 reported types of attack tactics which include 178 attack techniques and 352 attack sub-techniques.
A typical APT often goes through the sequence of external resonnaissance, gaining access, internal reconnaissance, expanding access, gathering information, information extraction, control of information leaks and erasing tracks.
APTs and Insider Threats are hard to catch by traditional anti-virus and malware detection. Organizations need a sophisticated, self-defense strategy such as Graphen CyberImmuneto protect them from such advanced attacks.

Graphen APT Cybersecurityis deployed at one of the top three Chinese banks at their NYC branch as their their internal cybersecurity system. It has proven to: